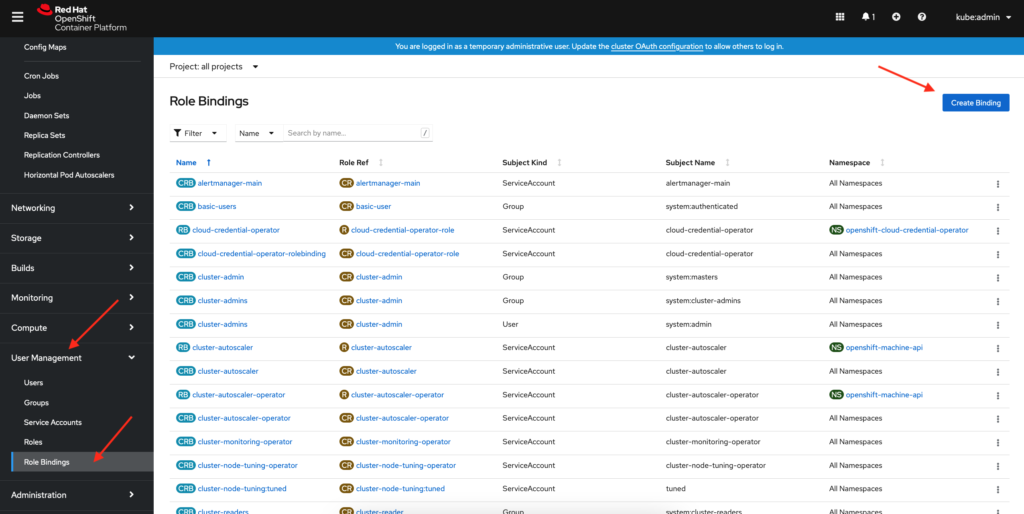
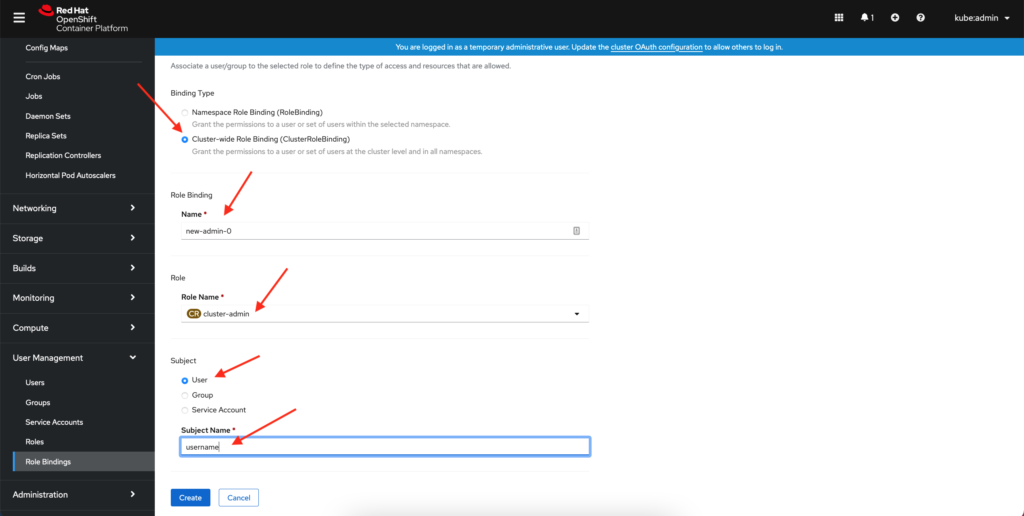
In the last blog post we went over how to add users to cluster-admin role in your OpenShift 4.x cluster. In this post I will detail how to make a user a cluster admin using the CLI which I have found to be the quickest method of doing so.
First we will have to log in to the cli using the kubeadmin user to provide cluster-admin level access to the accounts we created before.
oc login https://api.ocp4.example.com:6443Now that we are logged in as kubeadmin, let’s grant cluster-admin access to a user account.
oc adm policy add-cluster-role-to-user cluster-admin <username>Once you have done this for all users who need cluster-admin level access let’s login using that user using the oc login command from above. Let’s check that we have cluster-admin access by running the following command.
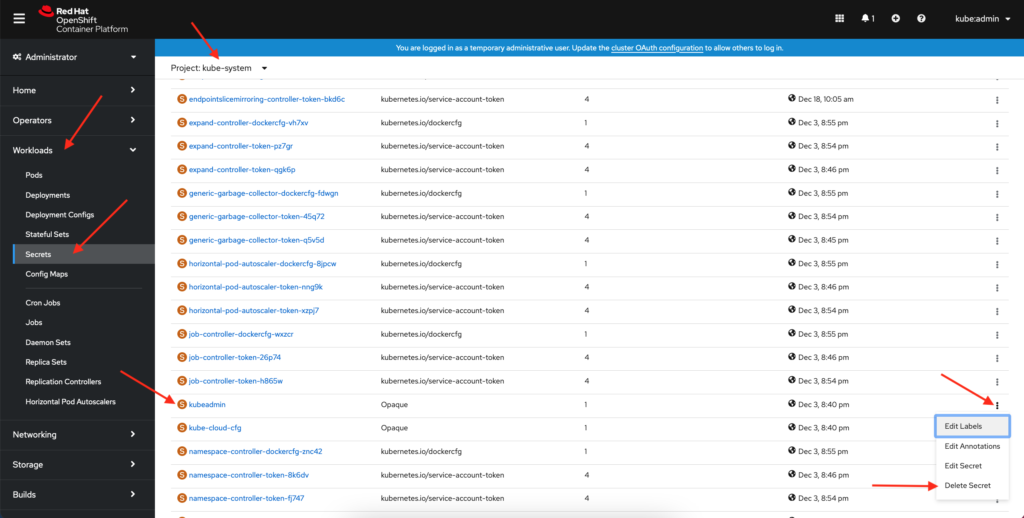
oc get nodesThis should return the names of the supervisor and worker nodes if successful. Next we will want to remove the temporary cluster-admin kubeadmin. We can do this by running the command below.
oc delete secrets kubeadmin -n kube-systemCongrats you have now setup your OCP users and given them cluster-admin access while removing the default account.
-Mike